Central Source Propagation Commonly Utilized Which of the Following Protocols
GATE GATE-CS-2015 Set 3 Question 65. Allow the water to settle the soil fill the hole and lightly tamp the soil with your hands to close any air pockets.
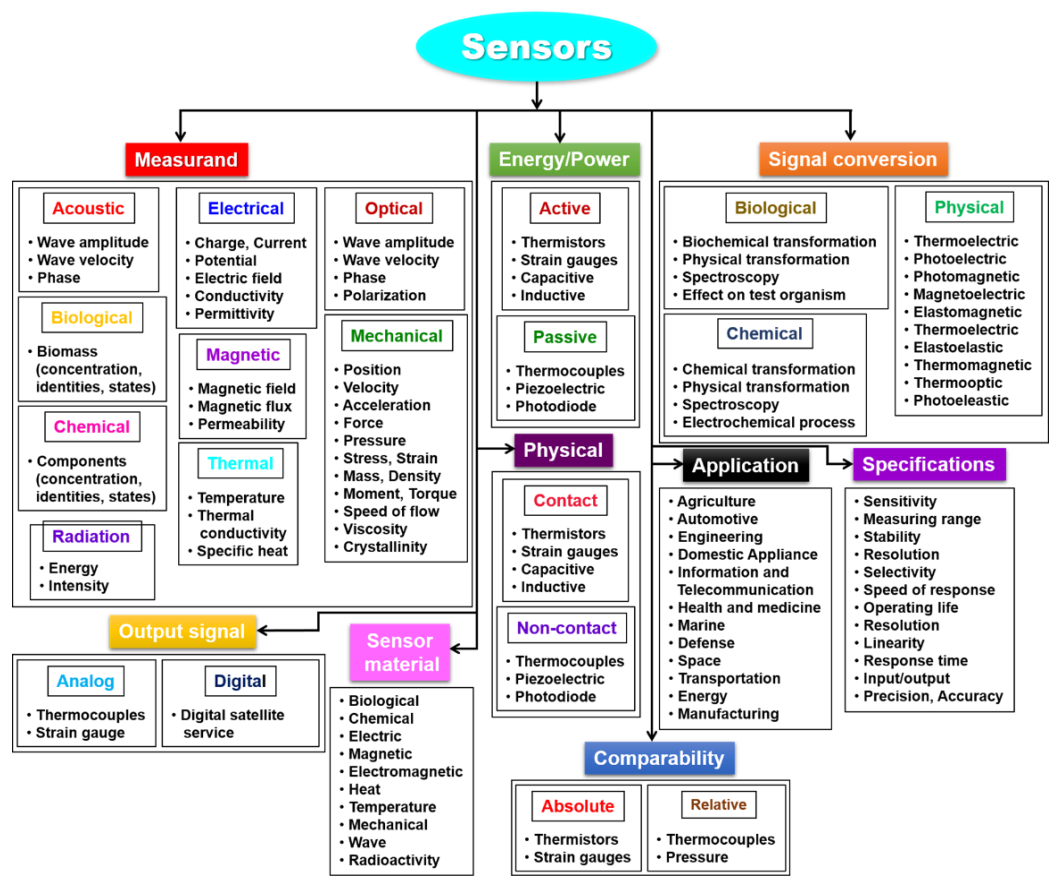
Sensors Free Full Text A Review On Biosensors And Recent Development Of Nanostructured Materials Enabled Biosensors Html
Hypertext Transfer Protocol HTTP The HTTP is the foundation of data communication for the World Wide Web.
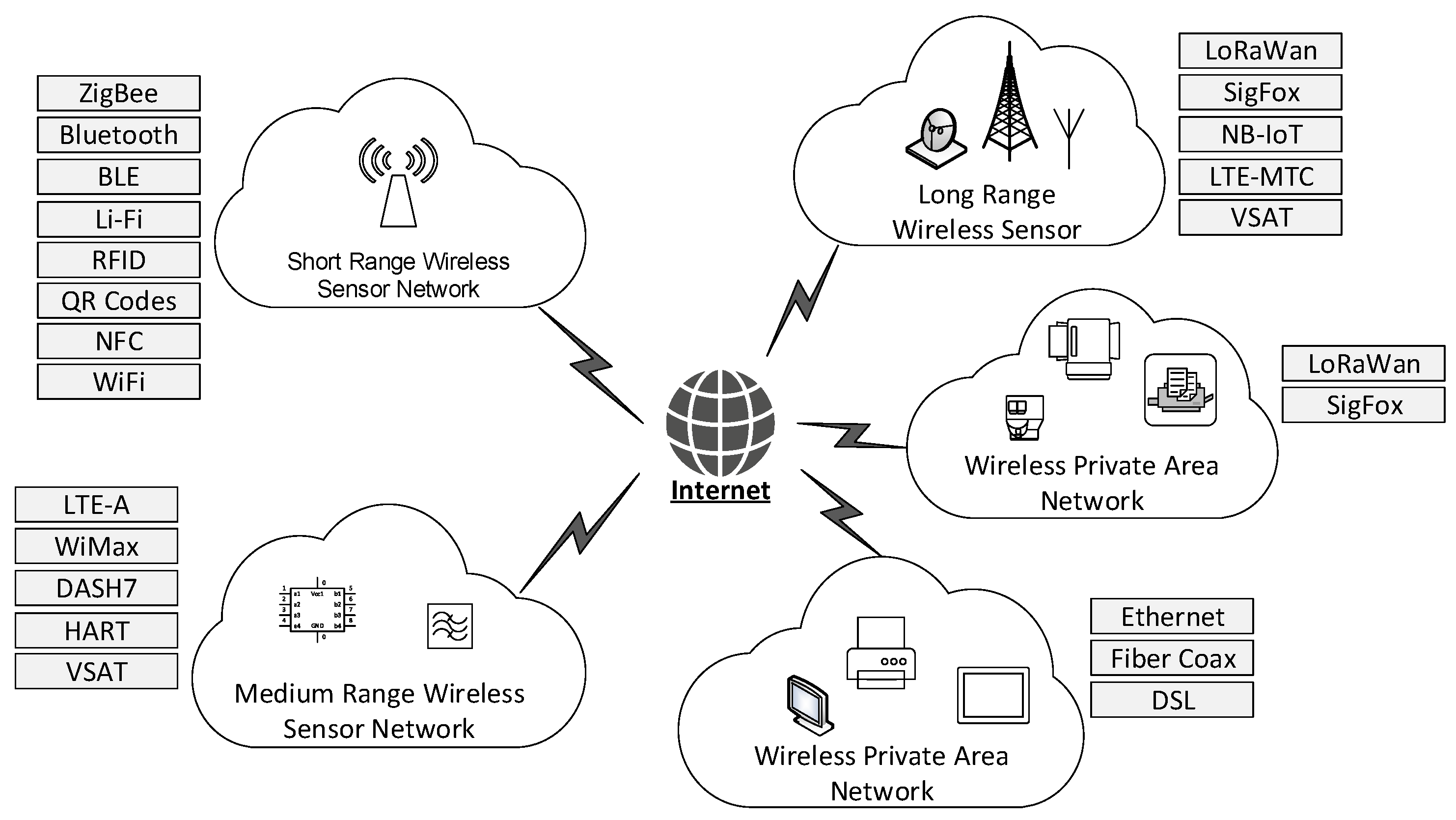
. Never leave the roots exposed to sun heat or wind. There are three components of information security that are ensured by cryptography. Filters network traffic by IP address targeted port numbers and communication protocols.
Which dynamic routing protocol was developed as an exterior gateway protocol to interconnect. NGINX Central Source propagation commonly utilized which of the following protocols. The transmission time of the acknowledgement frame is negligible.
The HTTP is the application protocol for distributed and collaborative hypermedia information system. Flags drastic changes in traffic flow rates. What single access list statement matches all of the following networks.
Central Source propagation commonly utilized which of the following protocols. Fill halfway with amended soil and water again. RDP RPC FTP TFTP During this type of an attack the attacker takes over a DNS server and changes the DNS settings so that all the requests coming to the target web server are directed to the attackers own malicious servers.
Stores traffic flow data in a graph showing traffic flow rate vs. Confidentiality which uses encryption algorithms to encrypt and hide data. A channel has a bit rate of 4 kbps and one-way propagation delay of 20 ms.
Place the plant in the hole. Pages 50 Ratings 100 11 11 out of 11 people found this document helpful. School University of Maryland University College.
The propagation speed of the media is 4 10 6 meters per second. There are literally thousands of protocols supported in the TCPIP stacksuite. Copying attack toolkit can be supported by simple port listeners or by full intruder-installed Web servers both of which use the Trivial File Transfer Protocol TFTP Autonomous propagation.
Water once again. In the central source propagation mechanism the attack code propa- gates from a central server to the compromised machine as shown in Figure 4 a. From the attackers perspective such central sources can be easily identified and disabled by security professionals.
Because standard access lists only filter on the source IP address they are commonly placed closest to the destination network. It is needed to design a Go-Back-N sliding window protocol for this network. Microsoft IIS 5 points Unsaved Central Source propagation commonly utilized.
Which type of network cover a large geographical area and usually consists of several smaller networks which might use different computer platforms and network technologies. RDP RPC FTP TFTP During this type of an attack the attacker takes over a DNS server and changes the DNS settings so that all the requests coming to the target web server are directed to the attackers own malicious servers. An example of this is a 1i0n worm which.
FTP - File transfer protocol which is used in central source propagation to install the tool kit from the central source which is located on the another. Section 3 Understanding Common TCP IP Attacks. Places information in the frame that identifies which network layer protocol is being used for the frame.
All groups and messages. Enables IPv4 and IPv6 to utilize the same network interface and media. The bandwidth of the network is 500 10 6 bits per second.
However only a few of them are related to security have native security featuresbenefits and are included on the CompTIA Sec exam. Central source propagation back-chaining propagation and autonomous propagation. The hypertext is structured text that uses hyperlinks between nodes containing texts.
Water again immediately before lifting them. The following material focuses on those protocols specified in the official Security 2011 objectives list. What action will occur if a switch receives a frame and does have the source MAC address in the MAC table.
A Low Propagation Delay Multi-Path Routing Protocol for Underwater Sensor Networks For the single-path scheme each node can not receive and send the. Hence this method is. Adds Layer 2 control information to network protocol data.
In this technique attacker places attack toolkit on the central source and copy. The only address that this device has is a MAC address. Malware propagation takes place quickly in the initial stage and later on it reduces as the number of new IP addresses available will be less as the time passes.
The following lists some dynamic protocols and the metrics they use. To get a channel efficiency of at least 50 the minimum frame size should be A 80 bytes B 80 bits C 160 bytes D 160 bits Answer. NTP Network Time Protocol The Network Time Protocol is used to synchronize the time of a computer client or server to another server or reference time source such as a radio or satellite receiver or modem.
Choose all that apply Question 18 options. Back-chaining propagation. O SYN flood attack o ACK flood attack.
RPC- Remote Procedure call which is used in the central source propagation to buffer overflow attacks used to inject the malicious code into the vulnerable system and make them executed. Central source propagation This mechanism commonly uses HTTP FTP and remote- procedure call RPC protocols 21. Like other file-transfer mechanisms this mechanism commonly uses HTTP FTP and RPC remote-procedure call protocols.
Availability which ensures that data is accessible. Choose all that apply Question 18 options. Routing Information Protocol RIP - Hop count Open Shortest Path First OSPF - Ciscos cost based on cumulative bandwidth from source to destination Enhanced Interior Gateway Routing Protocol EIGRP - Minimum bandwidth delay load and reliability.
Consider a network connecting two systems located 8000 kilometers apart. Following are some of the protocol attack techniques. Course Title CMIT 321.
Common protocols that use RARP are BOOTP and DHCP. Integrity which uses hashing algorithms to ensure that data arrives at the destination unaltered. 192168160 192168170 192168180.
The channel uses stop and wait protocol. Microsoft iis 5 points unsaved central source. Common Protocols Used and Their Ports.

Internet Protocol Suite An Overview Sciencedirect Topics
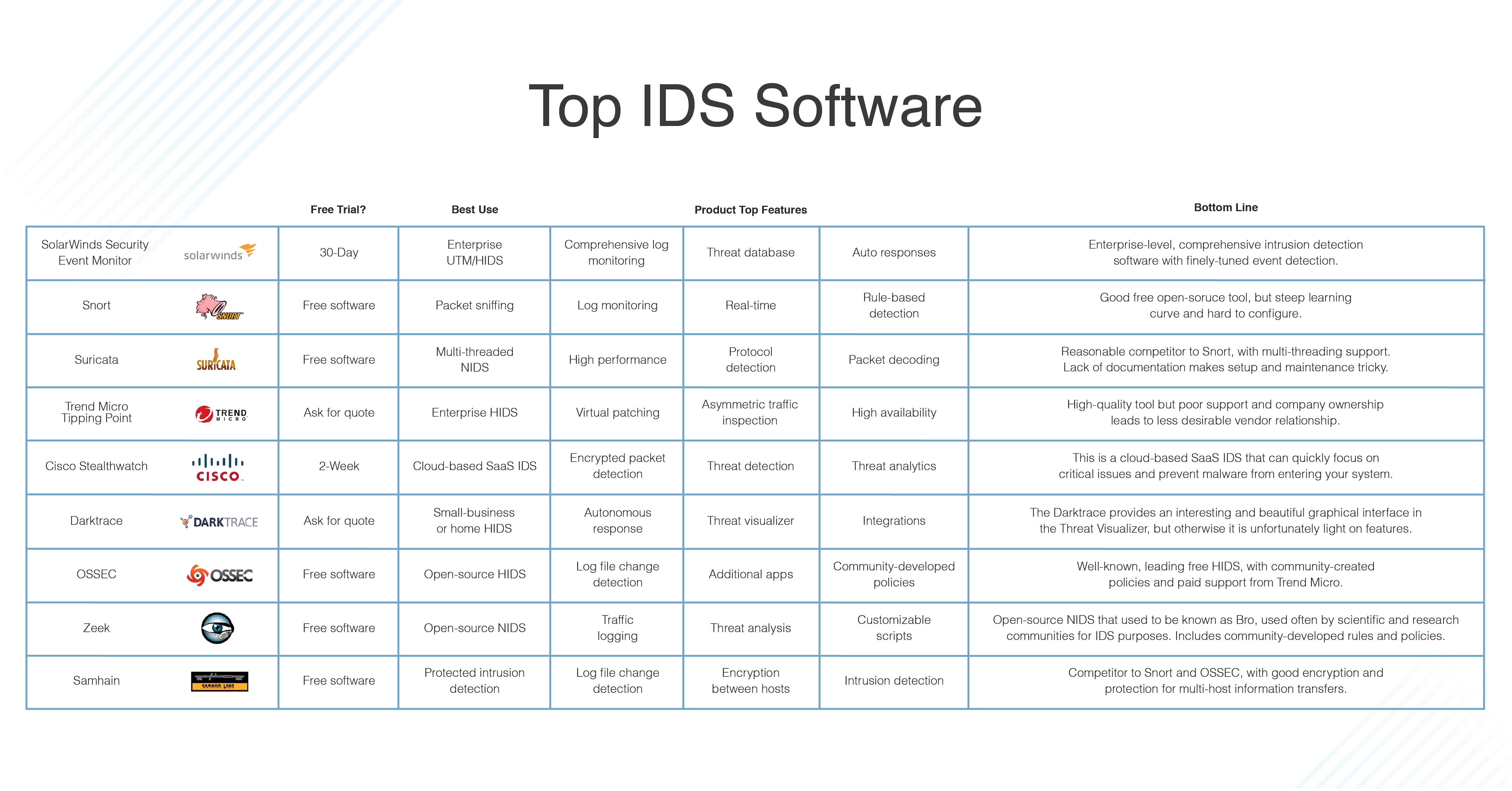
What Is An Intrusion Detection System Definition Types And Tools Dnsstuff

Electronics Free Full Text A Review Of Intrusion Detection Systems Using Machine And Deep Learning In Internet Of Things Challenges Solutions And Future Directions Html

No comments for "Central Source Propagation Commonly Utilized Which of the Following Protocols"
Post a Comment